Today, the 15th May 2017, Indian corporates, including Banks will be switching on their computers with a prayer in their lips hoping that they would not see the dreaded “Your files are encrypted” screen.
It is still not clear what would be the extent of damage that the ransomware could cause. The first version was killed. But it is reported that a modified version which does not have the kill switch is now in circulation. It could spread like a worm in a networked computer, self replicate and execute an encryption code remotely. Most major anti virus manufacturers have claimed to have included a ransomware protection tool either as part of their end-point security software or separately.
The first task for all IT users particularly those who are using Windows systems is to check if they have installed the patches provided for Windows and the Anti Virus software that they are using. They should not open their computers to internet before this task is accomplished. In this process, it is expected that most ATMs in the country will remain shut off today and create a mini cash crisis for Indian citizens who are running around. Consequently there will be a more than normal crowd in the Banks also where also the servers may run slow. We therefore may find some confusion in the financial market.
Unconfirmed reports are suggesting that many Banks including Syndicate bank, Union Bank, SBI, Karnataka Bank have been affected by the ransomware. Even HCL is reported to have been affected. I hope this report is not true as otherwise there would be chaos in the Banking industry today which will extend to the stock markets by the afternoon.
CERT-IN has announced a webcast to make companies aware of the issue which those interested may attend. The webcast may be available at webcast.gov.in. It may be difficult to access in view of the network related issues but it is worth trying.
CCN-CERT of China has issued a prevention tool which may be available here which security professionals can check.
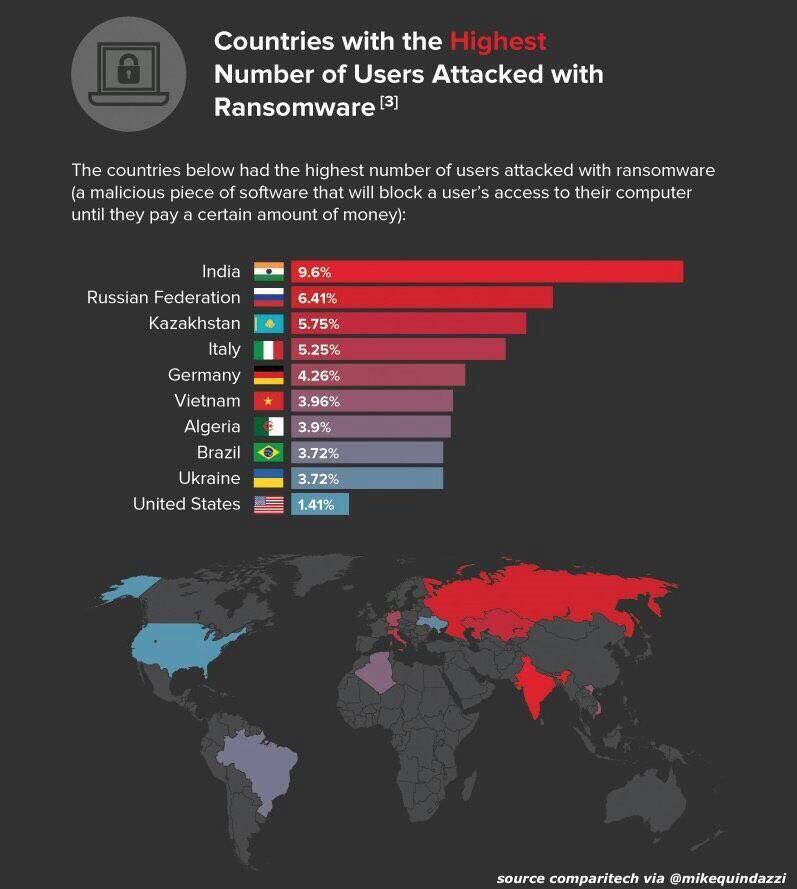
Amidst all the confusion it is necessary to note that one of the reports indicate that India is one of the countries with the highest number of infections.
Initially the breakout was observed in UK and Europe where there is a large number of infections particularly in the heath care sector. Indian impact may be yet to unfold. If the above report is true then nearly 10% of the infections are in India and we will come to know about the impact some time during this week.
We are concerned that the GST systems and UIDAI systems may also need to watch out.
The UIDAI system may not get affected since it’s design may prevent infection if normal precautions are in place. But the fact that the Iranian nuclear systems which were “Air gapped” and operating hundreds of feet below ground under utmost military security could be affected by Stuxnet means that no system is really safe as long as there are employees who are ignorant and negligent.
We may recall that the Stuxnet which was perhaps developed by US/Israel to attack Iranian Nuclear program also infected (Reportedly) the Rare Earth Minerals near Mysore, in Karnataka, India. Similarly WannaCry may also ultimately reach the GST systems and UIDAI. GST is yet to start but some testing is on. It is good if they take special steps to secure this nationally critical information system.
What is tragic is to note that “Shadow Brokers”, the group which released the weaponized cyber exploitation tools developed by NSA, a couple of which have been used in the creation of WannaCry have released further exploits from the hacked NSA stable in the last few days which may result in newer attacks.
Thus the source of all the chaos that is occurring in the Cyber world today is NSA. The speed with which the ransomware spread in Europe and the fact that US itself has not been affected as much as other countries indicate that most probably the infections had taken place earlier than when shadow brokers leaked the information and exploitation occurred now. It is possible that US had already infected systems in Europe and other countries as a part of its “Cyber Military Exercise” and when the exploits were used by the criminals, the victims had no defense. It is like a Military exercise preparation for which a stock pile of weapons were kept ready and terrorists took over the stockpile of weapons and used it for their own gains. It is a replay of a typical movie plot. Unfortunately we donot have a James Bond to enter in time to destroy the terror infrastructure before the real damage is done.
The Government of India and other affected countries need to take up the issue with the UN and question the US intentions. Is this in any way linked to discrediting Mr Trump? . Is it linked to the change in the FBI Director in US? …etc are also questions that bug our mind.
If US wants to stockpile Cyber weapons, it is their duty to secure them and not let hackers hack into their stockpile and endanger other countries. US should therefore take up a part of the liability for this Cyber attack and I request India to raise this issue in the appropriate forum.
For the time being we keep our fingers crossed and wait to see how the impact of the ransomware unfolds in India.
Naavi
Related Articles
MeitY reaches out to RBI, others against Wanna Cry ransomware
Cyber experts working round the clock to protect India from the ‘biggest ransomware’ attack
Revealed: The mysterious case of ‘Shadow Brokers’ and NHS hacking
Seriously, Beware the Shadow Brokers
U.S. Government Fears a Monday Explosion of the Ransomware Plague It Helped Create
China and Japan wake up to the Attack…
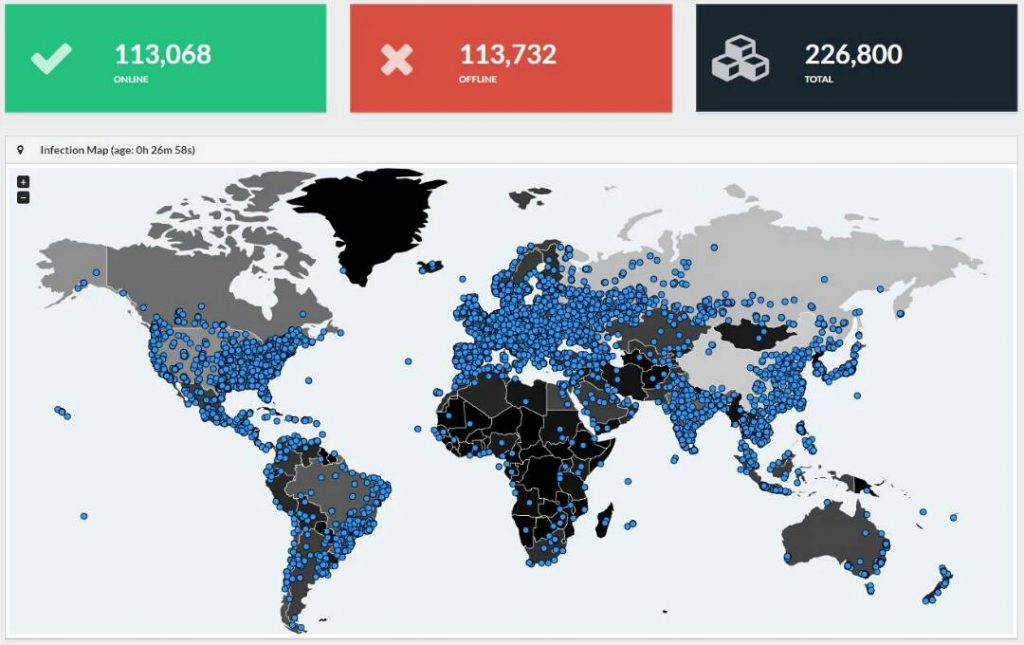
Update at 8.52 AM
The new infection map in the last 24 hours given below indicate that a large number of Indian computers are infected. Even US is now getting affected probably because we are dealing with a Worm that travels across the network and today US systems are also connected worldwide.