A ransomware attack which crippled many hospitals in UK is now creating waves of alarm by spreading into other countries. According to one researcher, more than 45000 attacks have already been flagged in 74 countries of having been caused by a ransomware by name WanCry or WCry.
The ransom demand is reported to have begun with around $300 to be paid in the form of Bitcoins. In an related development the Bitcoin exchange rate has spiked to US $1850 on May 12 and is presently hovering around US$ 1650. The ransom demand says that the ransom will double if not paid within 3 days and the encrypted files will become unrecoverable after a week.
Though no report of largescale infection has yet been reported from India, the infection map indicates that India has also been affected. The map shows infected computers that attempted to communicate with the server between 11 a.m. and 6 p.m. Eastern time on Friday according to NY Times.
It is stat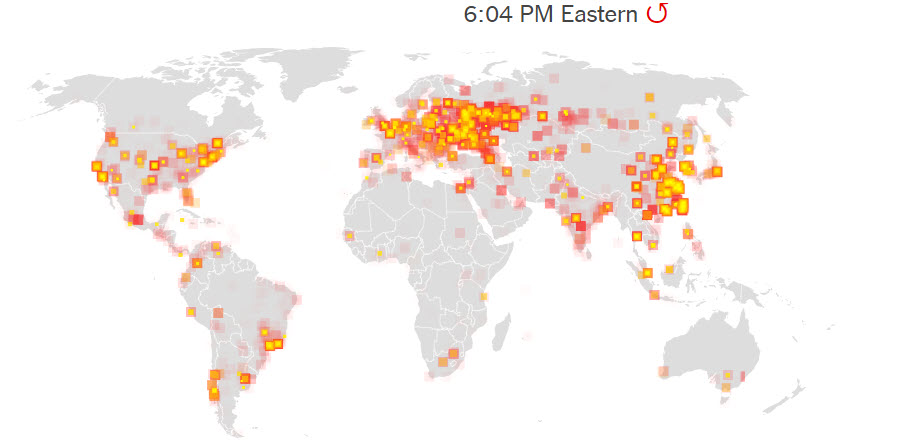 ed by experts that the ransomware exploits a vulnerability which was identified and used by National Security Agency (NSA) of USA to infect user’s computers as a part of its intelligence activities. Recently in April, a bunch of such Cyber Tools used by NSA were leaked by the underworld and it has now been exploited.
ed by experts that the ransomware exploits a vulnerability which was identified and used by National Security Agency (NSA) of USA to infect user’s computers as a part of its intelligence activities. Recently in April, a bunch of such Cyber Tools used by NSA were leaked by the underworld and it has now been exploited.
It appears that the exploit has hurt companies which have not applied one of the latest Windows patches. Also some anti virus companies are claiming that they already have the exploit covered in their product and hence the lack of adequate security measures by the users may be one of the main reasons why the attack has succeeded in the current proportions.
According to Kasparesky, “It’s important to understand that while unpatched Windows computers exposing their SMB services can be remotely attacked with the “EternalBlue” exploit and infected by the WannaCry ransomware, the lack of existence of this vulnerability doesn’t really prevent the ransomware component from working. Nevertheless, the presence of this vulnerability appears to be the most significant factor that caused the outbreak.”
Naavi.org had warned the IT users that Ransomware attacks are nothing but “Cyber Terrorism” and we need to guard against such attacks through various means including keeping an “Off Network Back Up”. Kasparesky advocates use of its “System Watcher Component” and other prominent Malware detection softwares also have suggested some added security features to be subscribed.
It is essential for all IT users to explore the feasibility of protecting their computers and the data through appropriate measures suitable to them.
Issues Raised By this Incident
The incident raises at least two main ethical issues that the society needs to address. First is that if NSA was aware of this vulnerability got some time, should it not have disclosed it and helped the safeguarding of the society rather than keeping it to themselves as a tool to watch terrorists. it is like the security agency having intelligence of a bomb attack but keeps the information itself until the citizens suffer by the execution of the attack while the agency was only trying to gather more information from its informers.
The attacks have now affected hospitals and must have caused even death of individual citizens. It has caused economic loss which is not limited to US$ 300 per infection (estimated total equal to US $ 30 million (Rs 210 crores) and the follow up costs.
Should this have been prevented by NSA by getting the vulnerability patched? Did they do it selectively to critical sectors?, Did they share the information with security agencies of other countries? are questions which will never be answered. NSA may however defend their position that in the larger interest of a need to watch the terrorist actions such as what happens in Syria or Pakistan, it is necessary to hold available Cyber tools as secret weapons to be used by the State only. Unfortunately the tools were not secured and was therefore used by exploiters. This is a typical scenario like terrorists of ISIS getting hold of Pakistani Nuclear weapons and causing damage to others.
The second ethical issue is whether the Victims should pay the ransom? ..and use Bitcoins?… thereby emboldening the attackers further and legitimizing the Bitcoin as a currency?
It is difficult to preach the victim who may have only the short term selfish interest of recovering his data at $300 rather than spending more subsequently.
But we understand that some Cyber Insurance Companies are paying claims for such ransom payments which in our opinion both unethical and illegal. Cyber Insurance claim even if higher than $300 should be paid for recovery of the data without paying the ransom and not for paying the ransom.
I urge all Cyber Insurance companies not to encourage payment of the ransom than the higher data recovery cost in the long term interest of the society. Of course, they should encourage their insurance customers to adopt better security preparedness by not only using the available prevention tools but also an effective disaster recovery mechanism and upgrade of patches.
Also after April 14, 2017 when the hackers are reported to have published a suite of NSA exploits, it is interesting to know if any Cyber Insurance company advised their customers about the possible risks ahead. This alert generation is normally the role of a CERT. But I expect Cyber Insurance Companies to be CERTs for their own interest.
I also would like to know what action CERT IN took after April 14 when NSA exploits were available and now after May 12 when the UK attacks became public.
Other regulatory agencies like RBI should also start sending their own advisories to their subordinate stake holders.
Action To Be Taken
In the meantime it is the duty of each IT users big and small and more importantly the critical sectors like the Hospitals, Banks and Government to review their security measures today.
I expect all listed Companies who are stake holders to report to SEBI if they are holding an emergency Board Meeting today to assess their security positions. If not SEBI should itself advise the companies to disclose their vulnerabilities and action taken in the context of the knowledge of this Cyber attack now available.
The compliance requirements under different law require that when a “Knowledge of a Risk becomes known, appropriate remedial action needs to be initiated”. So all CISO s need to wake up and work over time this week end and ensure that the threat perceptions are updated for their management to take immediate action. Even if the Managements donot ask, CISO s should shoot out an e-mail to the Board members to hear out an assessment presentation and take remedial action.
If necessary, simply forward the copy of this article to your CEO since bringing the risk to their knowledge is part of the “Due Diligence” of the CISO.
Naavi
Related Articles:
In Naavi.org: Start a War on Ransomware. It is Cyber Terrorism
Hackers Hit Dozens of Countries Exploiting Stolen N.S.A. Tool
Alarm grows over global ransomware attacks
WannaCry ransomware used in widespread attacks all over the world
NHS left reeling by cyber-attack: ‘We are literally unable to do any x-rays
UPDATE: 13th May 2017: 12.45
In an interesting development, one security researcher has found and executed a kill switch that seems to have stopped spread of the WannaCry ransomware. He found the hard coded code indicating that the ransomware would stop if a random domain name named therein becomes live. It is presumed that the code writer wanted to hold the power to stop the ransomware and had introduced this kill switch. This was identified by the security researcher who checked up the domain name and found that it was available for registration. He registered the domain name and the ransomware died.
See the report here: Accidental hero’ finds kill switch to stop spread of ransomware cyber-attack
Wish all cases of malware were solved so quickly. We must however congratulate the person responsible for killing the ransomware….may his tribe increase!
Update: 13th May 2017 : 1452
In a tweet the person who identified the kill switch says that he was not aware that the registration of the domain would act like a kill switch. It was therefore an accidental discovery.
This is interesting to note because if the domain name was indicated in the hard code and it was found to have been registered in the name of the security expert, he could have been connected with the writing of the ransom ware code. He had unknowingly created an incriminating evidence against himself. It was fortunate that it turned out to be a blessing in disguise.
CERT IN now issues an alert
It appears that CERT In has now issued an advisory which is a replica of what Kasparesky and others have given. Hopefully next time CERT IN will be quicker. RBI and SEBI also needs to issue an advisory of their own or link to CERT In.







