In the past we have highlighted the three dimensional approach to Information security which combines Technical, Legal and Behavioural science as the dimensions of Information Security.
Uni-Dimensional Approach
Information Security has often been approached as a “Uni-Dimensional” concept based on “Technology”. Under this concept, Information Security is often defined as “Preserving the Confidentiality, Integrity and Availability” of information. This is often referred to as the CIA principle.
Of late the Information Security community has extended this three component based technology approach to the fourth component of “Authentication”.
This “Uni Dimensional” approach works on the end objective of “Protecting Data” and “Restoring it in the event of a loss”.
The approach therefore depends on the DRP-BCP principle where there is a good (if possible concurrent) back up of data which can be restored “Fully” within a short time. The Backing up process and the Recovery from Back up also needs to be “Verified” with hash check.
In these days when “Trojans” are programmed to activate themselves on pre-determined time and day, it is also necessary for the restoration from back up to be done as a “Clean Back up” ensuring that no dormant malware is present in the back up copy and using a clone copy for restoration if required.
This Full, Verified and Clean back up process can solve the problem of data loss and if the BCP process is set to low RPO and RTO (Recovery point objective and Recovery Time Objective), the Uni dimensional information security approach of “Protecting the Data” can be reasonably satisfied.
The implementation of the Uni Dimensional technology based approach is through the Firewalls and IDS systems as well as the Access Control and Encryption kind of technology applications. Hashing and Digital Signature technologies are used to ensure integrity and authentication.
The ISO27001 and PCI DSS type of information security audits are normally considered as the final word on information security in this Uni-Dimensional approach.
Dual Dimensional Approach
The Uni-Dimensional approach essentially tries to protect the “Data” from being lost through unauthorized access or through other technical issues including malware attacks such as the ransomware.
However when the unauthorized access results in ex-filtration of data or compromise of confidentiality, mere restoration of lost data may not provide a relief to the information owner. When data held in trust by a company is compromised, then there is an issue of third party liabilities arising out of privacy protection laws or contractual obligations.
There could be also vicarious liabilities arising on the information owner due to the legal provisions such as under Section 79 or 85 of ITA 2000/8. Essence of such legal provisions is that if an organization that collects information from the public suffers a data breach through external attacks or insider threats, if it cannot prove that it has observed “Due Diligence” and/or “Reasonable Security Practice”, the liabilities will crystallize on the organization and its executives.
Such liabilities (Section 43 read with Section 66, Section 43A, Section 72A, Section 65 and Section 67C) could result in bot civil liabilities and criminal liabilities.
Hence a DRP-BCP which results in restoration of data and continuity of business systems does not protect the information owner from either being liable to pay damages or even go to jail.
The Second dimension of information security therefore is the “Techno Legal Approach” which tries to protect the information owner from liabilities arising out of data breach incidents. Such protection arises from the organization being “ITA 2008 compliant” and also documenting its compliance process to be produced as its defense when the requirement arises.
Being able to protect one self from liabilities is the “Defensive Legal Remedy” (DLR) that companies may seek from its compliance activities under the Techno Legal Information Security approach.
Apart from being able to defend the company from liabilities, being compliant with cyber laws ensures that the company may be able to use the same law to recover damages from others (eg sub contractors and ultimate offenders who committed the crime) through invoking a litigation process. This is an “Offensive Legal Remedy” (OLR) that becomes available to the company which has suffered a data breach.
It is clear that no company can claim to be legally compliant under “Due Diligence” or “Reasonable Security Practice” if it has not implemented the technical security measures including obtaining certification of ISO 27001 or its equivalent.
However the technical security measures are considered “necessary but not sufficient” to provide the liability protection for the information security owner.
Thus the Dual Dimensional approach extends its scope from protecting the information along with the information security owner.
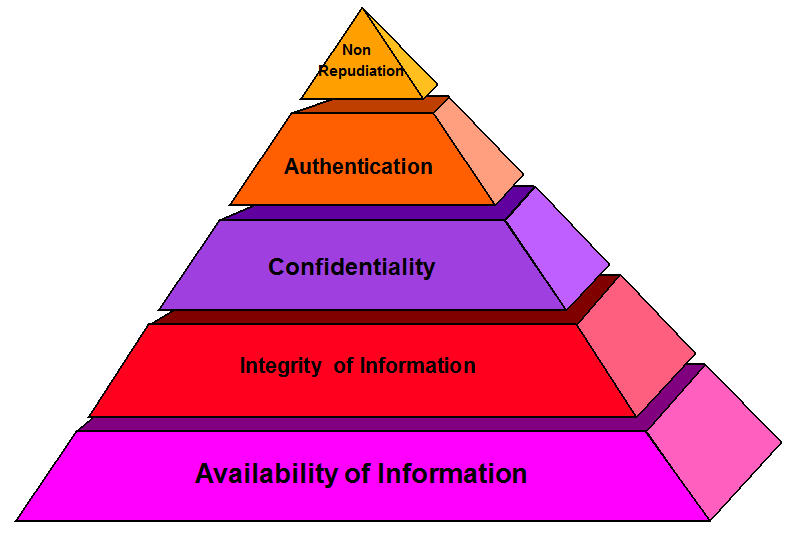
The Preservation of Confidentiality, Integrity and Availability of information still prevails along with Authentication which should be legally sustainable and “Non Repudiable”.
Undersigned believes that the management approach to information security could be prioritized based on the following hierarchial prioritization of the different components of Techno Legal Information Security.
The Third Dimension
Whether the approach is Uni-Dimensional or Dual Dimensional, the implementation always requires the support and complete willingness of the people. The technical aspects such as access control often fail because the users tend to be ignorant and negligent. Policies and procedures prescribed for legal compliance which may include sanctions also fail through ignorance and unwillingness to adhere to rules and regulations.
Information Security professionals do recognize the role of “People” in information security and try to address the “Social Engineering” attacks through appropriate awareness building exercises within their employee fold.
However, problem with “People” is that same persons behave differently at different points of time and different persons behave differently for the same stimuli. It is for this reason that the undersigned considers “Behavioural Aspects of people” as the third dimension of information Security and not merely the “people”.
“Ignorance” can be reduced by “Awareness” building which is through training of various types that are part of the information security practices.
However, Awareness Building is another “necessary but not sufficient” factor in information security implementation. Awareness needs to be converted into “Acceptance” and there after into “Commitment” if the information security controls are diligently to be followed by the people who are responsible for the implementation of information security.
Since law attributes the automated actions of a system to the “Person who caused the system to behave in the particular manner”, the software creator or the owner of the system who takes over the software/system along with its default configurations become the human elements who are responsible for the actions of the automated systems. But the software developers may not foresee the vulnerabilities nor feel the effect of the vulnerabilities since they successfully pass on the liabilities to the user. Law hurts the user of a software and the intermediary who provides the platform for the software. It does not touch the software developer who developed and released a defective software with vulnerabilities. Though the software developer may later identify the bugs and send “Patches”, the liability on “Zero Day Liabilities” still remains with the software user which is an unfair burden to some body who has paid for the software.
Some software developers have the ethical attitude to at least run “Bug Bounty” programs which acknowledges the limitations of the testing process before release of the software but tries to provide some cover to the crowd sourcing of testing process. But since Bug Bounty programs are not mandatory, most software developers release untested defective software and start counting cash before the product is patched for basic defects.
“Security By Design” and “Secure Coding Practice” is known to most software professionals but they still ignore. This is a serious issue that the software industry has not been able to tackle effectively.
This attitude to ignore security issues is more a result of the “Attitude” of the software professionals rather than a function of “Ignorance”. There are issues arising out of “Technology Intoxication” and some times a deviant mindset such as the “Cyber Offendo Mania” (an Obsessive compulsion to commit an offence).
In the Cyber Crime scenario, attitude of users to “Blindly Trust” the software and an urge to “Be the first to test a new introduction” often makes people invite compromise of identity and opening up doors of opportunity for attacks.
The attackers are also emboldened through the “Anonymity” and “Asymmetric advantage” that the he may use for planning and executing the attacks while the security professionals are constrained by the uncertainty and unpredictability of the nature or source of the next attack.
The attackers are also persons who are “Technologically intoxicated” and hence are prone to irrational decisions besides calculated motivated attacks.
The behavioural aspects of unknown attackers is not amendable to be mended except by creating a “Deterrence” through well publicized exploits of police in busting criminal rackets. However we can try to mitigate the risks of insider attacks by trying to modify the behavioural traits of people who work for an organization.
For this purpose, we need to be able to identify “Deviant Minds” and put in place strategies to mitigate the risks through counselling, advanced training etc.
Addressing the “Mitigation of Information Security Risks arising out of Behavioural Traits of employees” is a subject which is far removed from the skill sets that an information security professional is normally endowed with. Management/HR professionals may posses such skills but technical experts have skills which may be diametrically opposite to the requirements of observing and reacting to psychological infirmities of the subordinates.
This area is still in a developing stage and Psychological and Sociological experts need to research in the area of Information security challenges arising out of behavioral traits of people.
Naavi tries to incorporate principles of Behavioural Science solutions such as ego-gram mapping and script mapping of Eric Berne and identifies the requirements as part of his “Pentagon Theory of Information Security Motivation”. Under this theory, it is considered that Information Security motivation is bound by Five parameters namely Awareness,Acceptance,Availability, Mandate and Inspiration arranged as the boundary walls forming a pentagon rather than the hierarchial pyramid model of motivation used by Dr Maslow in his theory of motivation.
There are several issues of this theory which needs further examination by Techno Legal Behavioural Science Experts who are the Information Security professionals of the coming era.
The Plus One Dimension
Naavi has been discussing the three dimensional approach to Information Assurance for several years now and hence it is not new. The information security professionals in general have already moved from the Uni-dimensional approach to the dual dimensional approach. The hurdle to absorb and assimilate the third dimension will take some more time and will require managerial acumen to be imbibed by the CISOs. It will take its time and we need to wait for this maturity to be reached.
In the meantime it has become necessary to point out to another dimension which is relevant for the current scenario.
While the earlier approach covers protection of data and the protection of the data owner, there is also a need to consider whether it is the responsibility of the information security community to grow out from being selfish and always looking inwards to being more responsible to the community they serve by being a little more outward looking.
In this approach, it is necessary for the Information Security to consider if there is any risk for the eco-system caused by the information security failure and whether some thing can be done to protect the eco-system.
One example that comes to the mind is the discussions we are now having on “Bitcoin”. There are many information security professionals who endorse Bitcoin because they like the “Block Chain technology”. Some are even thinking as if Block Chain technology is a “Information Security Tool” since it can be used to “Build trust from out of an Untrusted resource”.
However, if Bitcoin is an “Anonymous” and “Unregulated” currency that can replace the legal tender of a country, the impact that it may leave on inflation, Black money creation, Terrorist funding etc needs to be taken into account. If these negative concerns outweigh the positive aspects of the technology, we should be prepared to reject the innovation. This is like the “Risk Absorption Capacity” of the society that needs to be kept in mind at the time of chosing risk mitigation strategies. If a certain risk is beyond the risk appetite of an organziation, such risk needs to be eliminated by avoiding the risk rather than trying to mitigate it through other measures.
The rush to implement Aadhar Based Payment Systems could be another innovation that we need to check under this Plus-one dimension. “Regulated Anonymity” vs “Absolute Privacy Protection as a Fundamental Right” could be another example that we need to check under this concept.
This concern for society and incorporating the “Social Cost Benefit” to our equation of information risk management is the “Plus One” dimension that I would advocate for the industry of information security professionals to consider.
Even the Cyber Insurance professionals should consider this as a necessity since the aggregated risks arising out of such damage to the society makes re-insurance more expensive.
This Plus-One dimension opens up a discussion on Technology innovators who tend to introduce “Irresponsible Innovation” that can cause “Disruption” which may actually lead to destruction of the society. Some of the Cybertariat issues that I have discussed earlier actually stem from the fact that technology innovators often blinded by their “Technology Intoxication” ignore the debilitating effect of what they do on the society of which they are also a part. This is the “Bhasmasura Syndrome”(Call it Frankenstien Monster if you like) which I espoused in an earlier article.
We as a community of Cybertariats including the software developers, information security professionals, management professionals, Cyber law professionals, Psychology/Sociology professionals etc should all start debating on the need to recognize and factor in “Social Cost” to technological innovations so that progress does not come at the cost of the society.
Naavi







Pingback: Theory of Dynamic Personal Data - Naavi.org