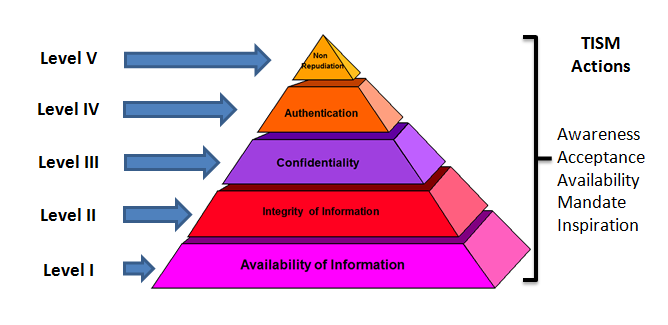
Information Assurance (IA) is a management initiative to ensure Confidentiality, Integrity, Availability, Authentication and Non Repudiation of information in an organization. Taking the practical difficulties involved in achieving a satisfactory level of IA, Naavi has suggested a “Total Information Assurance”(TIA) plan under a “Modular Implementation” strategy. The essence of this Total Information Assurance for Modular Implementation approach (TIA4MI) is to set up achievable milestones that the organization can effectively address in its IA program so that it can achieve its TIA objective in measurable steps.
The TIA4MF approach depicted in the above diagram envisages that the focus of the organization in Level I will be to ensure “availability” of information to meet its business needs. This will be followed by “Integrity”,”confidentiality”, “Authentication” and “Non Repudiation” in that order. In each of the target levels, the focus is on the Core objective of the level. However it must be remembered that the levels lower to the target level are deemed to be already addressed to a satisfactory level while concurrent implementation of higher level objectives are considered desirable.
Once an organization resolves to start a TIA program, it needs to go through the process of “Risk Analysis” to identify the risks and steps needed to mitigate the risks.
Risk analysis depends on the “Threats” and “Vulnerabilities” that exist in relation to the information assets of an organization. We must understand that “Vulnerabilities” exist within the systems and “Threats” arise from outside the systems.
“Vulnerability” represents a “Flaw” or “Weakness” in system security procedures, design, implementation or internal controls that could result in a breach of security either through a deliberate action or through an accident.
“Threat” on the other hand is the potential for such vulnerabilities to be exploited. Threats may arise from external sources and not under the control of the organization.
Many organizations who are in the process of adopting IT in their business are driven by the operational requirements and often donot factor in Information Security as a part of their IT objectives. As a result they reach advance levels of IT implementation without a proper incorporation of Information Security principles. When such organizations decide to undertake an IA program the management will suddenly realize that they donot know where to start from.
Of course they can start by inviting an external IA Consultant and start their IA program under his guidance. However it would be advisable for the organization to at least prepare the foundation from which they can have a meaningful dialogue with an IA consultant. The lack of understanding of the issues involved may make it difficult for the IA consultant and the organization to arrive at a mutually acceptable engagement. In fact the IA consultant will not be able to make a proper estimation of the efforts required for IA implementation and hence the dialogue may get frustrating.
In order to improve the quality of the dialogue with the IA consultant it is essential for the organization to develop its own understanding of the requirement of IA in their organization.
The very first step in this direction is for the organization to understand what is the information they are intending to protect in their organization and where are they located. In other words they need to “identify” information, “classify” it into different categories such as “Personal”, “Sensitive”, “Business” etc., and “locate” them within the organization.
This Idenitify-Classify-Locate exercise (ICL Exercise) is the first step that an organization needs to undertake in embarking on an IA program.
It is possible that even this ICL Exercise may require an organization to call in an external consultant for assistance. This should however be treated as an “Information Assurance Preliminary Study” rather than an “IA Risk Analysis”.
Some organizations may treat the ICL exercise as part of the IA Risk Analysis and expect the consultant to undertake the exercise. While there is nothing wrong in this approach, the problem arises when the organization does not understand the difference which makes it difficult for them to appreciate and accept the effort estimates that are required to be accepted before the consultant begins his work. Without completion of the ICL exercise it is also not possible for the IA consultant to arrive at the effort estimate.
These problems are more common in SMEs who are undertaking an Information Assurance audit for the first time and also in most of he E-Governance projects.
“ICL before IA” is therefore what Naavi suggests organizations to adopt as a management principle as they try to move from IT implementation to Information Security consideration.
Naavi
PLEASE NOTE:
This website has been in existence since 1998.
Older posts before the site switched to word press are available through the link at the top and here below.