Above picture is representative and has been created using Nanobanana AI tool
Above picture is representative and has been created using Nanobanana AI tool
The petitions from the Scrap DPDPA Brigade in Supreme Court refers to DPDPA 2023 and the Rules as not being in conformity with the famous K S Puttaswamy Judgement of the Supreme Court of 24th August 2017. (KSP judgement)
The essence of the decision in the case of KSP was that
“Privacy is a fundamental Right under the constitution and is part of Article 21 of the Constitution subject to the reasonable restrictions under Article 19(2). “
The bench however did not define Privacy nor gave any restrictive boundaries to the Right to privacy whether it is restricted to Information Privacy. It however extensively noted the risks related in information privacy. In its directions, it stopped at stating that the Right is part of the fundamental Rights and parts of M P Sharma judgment and Kharaksingh’s judgement are over ruled.
The KSP judgement did not further gave any order to the Government to pass any statutory law to protect the Privacy Rights of Indian population. Hence the statement of the petitioners in the Reporter’s Collective Trust that “DPDPA Act and Rules are in complete contravention of the law laid down in the KSP judgement” is incorrect.
Before this judgement was out, the Government had already formed the Justice Srikrishna Committee which went on to give its report in 2018 which after several iterations became DPDPA 2023.
DPDPA 2023 was under no obligation to define “What is Privacy” and “How the Government Protects Privacy”. Hence the Government chose to restrict the law as “Law for protecting the personal data” and went on to define personal data.
Privacy in India is therefore protected by the Constitution directly and DPDPA 2023 facilitates the Data Principal to protect his privacy by protecting his personal data with the deterrance mentioned in DPDPA 2023.
The Government also adopted a strategy different from GDPR and laws of other countries by designating the entity determining the purpose and means of processing of personal data as a “Data Fiduciary” placing on them the onus of understanding what the data principal wants and carry out his permissions. Hence Consent was the backbone of the law.
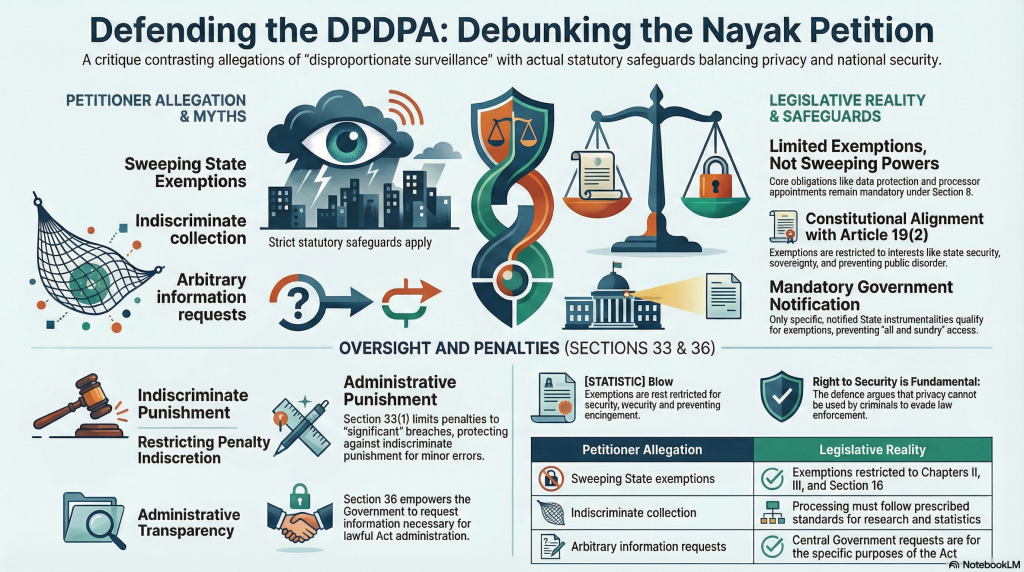
Since Article 19(2) prescribed the reasonable exceptions, Government also recognized “Legitimate Uses” under Section 7 and Exemptions under Section 17. Both Sections 7 and 17 are applicable to both the Government and the Private Sector. Some of the exemptions are partial exemptions. Legitimate use is conditional.
The only blanket exemption is related to some of the aspects of the Article 19(2). Even here, all exemptions available under Article 19(2) have been invoked. Government has been very conservative. Also 17(2) is applicable to only such instrumentalities of State which are notified. Unless an entity is notified, the exemptions are not applicable even for the approved purposes such as the interests of sovereignty and integrity of India etc
To call this provision as “Attempt for Mass Surveillance”,, “Excessive”, “Disproportionate” etc… is false.
The Call for scrapping of DPDPA is atrocious. DPDPA tries to make Data Fiduciaries responsible and not indulge in indiscriminate harvesting of personal data, use it for spamming, profiling etc. The industry is interested in monetizing the personal data of individuals without a fair compensation to the data principals.
DPDPA is expected to put an end to the obnoxious practice of Corporates stealing personal data without proper consent and enriching by their use. While DPDPA may not fully prevent the woes of the public from being targetted with Spams, Use of dark patterns to manipulate purchase decisions, use of techniques to change the freedom of mental decision making through mind bending communication strategies, it has given a hope to public that things may move in that direction.
The penalties at levels of Rs 250 crores are one of the highest in India but are no where near the international norms at 4% of global turnover to 10% of national turnover etc. The penalty structure under DPDPA does not mandate either Rs 50 crores or Rs 250 crores. It leaves the discretion to DPB to determine the penalty taking into account the capacity of the data fiduciary to pay. There is also a voluntary undertaking provision where penalty can be waived.
Without properly reading the law the petitioners make unsubstantiated statements including that journalists cannot pay the fine of Rs 250 crores and hence the law is unconstitutional.
This is an attempt to misrepresent the law.
The petitioners seem to place “Journalists” as if they are above law. Journalism has a public purpose and today most of the journalists are not the committed journalists of the yesteryear. They are under influence of money bags and politicians. Hence giving an unfettered freedom to them is a danger to the society.
Remember, Even Hindenberg can claim to be a “Research organization” as much as any other journalist.
Journalists who are also lawyers are persons who normally use RTI information for purposes other than public good. Even the NGOs they represent are often funded by international organizations and protect the interests of their foreign bosses more than Indian public.
We therefore seriously question the credibility of the petitioners who ought to declare their sources of revenue.
Bar Association also has to ensure that members of the Bar donot claim to be “Registered Journalists” and claim the benefits of the so called “Freedom of Speech” etc. This is a disguised attack on the society.
The NGOs headed by lawyers who say they are representing public interest should not be allowed by the Supreme Court to file PIL without proper scrutiny.
I wish the Supreme Court prevents the gross abuse of the PIL privilege used as a weapon against progress.
Lawyers are considered as officers of the Court but we wonder if they are more officers of vested interests often guided by commercial or political considerations using the Court as a play ground for meeting their objectives outside the Court.
Otherwise it does not make sense for any of the petitioners to ask for scrapping of DPDPA just to ask for some exemptions for the profession of their clients.
The petitions filed should therefore not be considered as PILs. They are petitions filed on behalf of the clients like an association of journalists or an association of RTI activists.
The real public advocacy champions are not capable of matching the expenditure required to fight their passions in the Supreme Court and have to often remain in the background. The Court should recognize this and bring such organizations forward and listen to their advice.
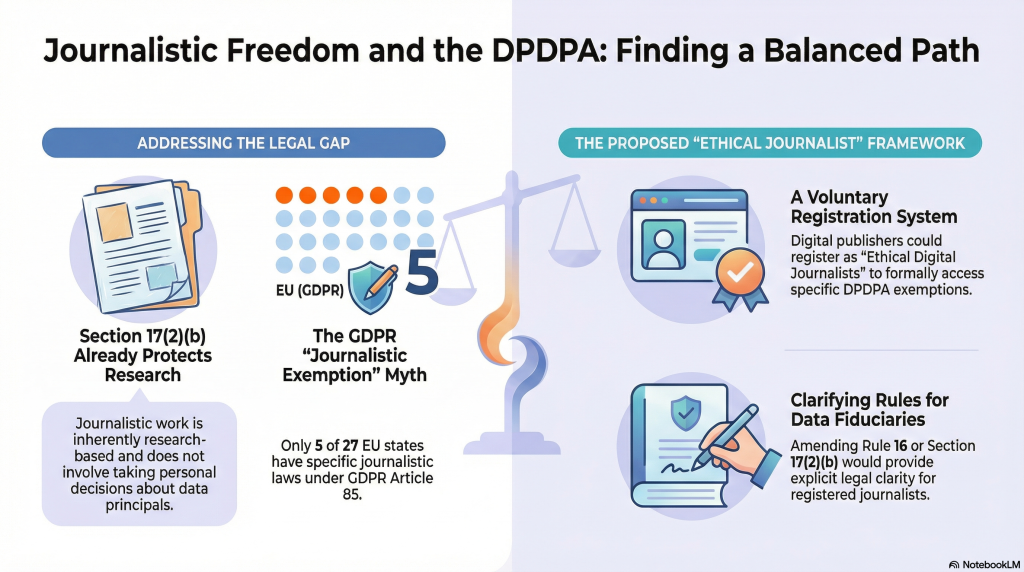
The concerns related to Section 44(3) or 17(2)(b) are easily addressable in the rules and have already been addressed. The petitioners donot want to see through the provisions with an open mind and are ascribing motives to every word in the Act and the Rules without justification.
It is our desire that the honourable Supreme Court does not allow such pseudo public interest champions misleading the Court through their oratory and professional standing.
Naavi