Ujvala Consultants Pvt Ltd has introduced a mechanism for self assessment of an organization for GDPR Compliance and arriving at a Data Trust Score which reflects the effectiveness of compliance.
GDPR has been in existence since 2018 and there are established mechanisms to implement a compliance system. ISO 27701 is in the forefront of this evaluation as an audit system. However ISO 27701 is an extension o ISO 27001 and could be difficult to adopt with by SMEs/MSMEs. Hence an attempt was made to establish a more affordable and modularly implementable system of “Gap Assessment”, “Summary Assessment” and “Certification Audit” through the DTS-GDPR mechanism (Refer ujvala.com).
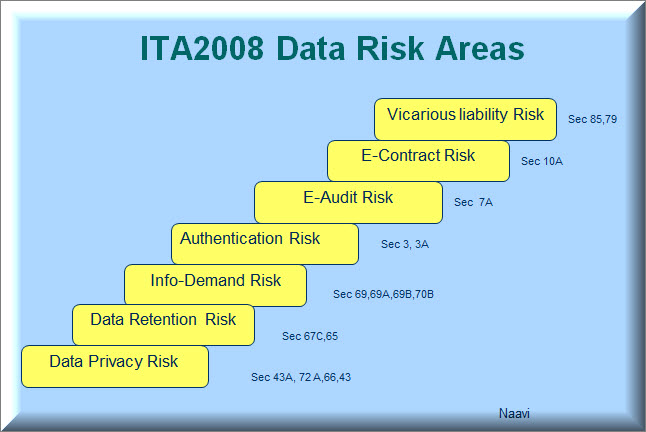
The system of reducing the compliance assessment to a number in the form of a DTS score is a concept introduced in the Indian law and not in GDPR. However there is no reason why this should not be applied to GDPR compliance assessment also as it brings some clarity to the complex mechanism of compliance assessment though it could be considered subjective to the auditor’s assessment.
After GDPR came into existence, there have been many online services which are like “Self Assessment Check List” and have been helpful to some extent. Ujvala’s attempt is not different from such services. However, in a techno legal compliance evaluation, it is difficult to keep the subjective evaluation of an expert out of the evaluation system. Hence any attempt to automate the assessment cannot avoid dilution of the assessment.
Ujvala DTS system acknowledges the inherent difficulty of a techno legal assessment based only on self assessment but tries to provide for better evaluation through the “Summary Assessment” based on scrutiny of policy documents before a proper audit examination can be made.
The system therefore uses a set of around 239 questions which are self answered by an organization. The objective of these questions is to enable the organization to reflect on their own systems and bridge gaps indicated by the questions. It is agreed that this self assessment is not good enough for third parties such as the Data Exporters to accept blindly. But it is a good starting point in the journey towards compliance.
When policy documents are submitted for review, Ujvala as a consulting organization needs to evaluate the policies and provide an “opinion” which is a “Reasonable Assurance” for the Data Exporter sitting in EU.
Additionally, Ujvala may expect certain basic technical tools to be adopted by the organization for better management of Privacy By Design and Default.
The effort of Ujvala is to assist the management of the organization to improve its own confidence regarding presenting itself as a “GDPR Compliant Organization” to the data exporters so that it can be a “Data Importer” and offer its services as a joint controller or data processor.
GDPR authorities are making their own efforts in ensuring smooth data transfers to “Non Adequacy” countries and this is taken note of by Ujvala as a guidance for implementation with the Indian data importers.
One such effort is the suggested “Certification as a tool of transfer”.
Under this scheme, it is envisaged that a specific data transfers can be enabled based on a “Certification” that the transfer carries the necessary assurance as required under Article 46 (2)(f) of GDPR.
Though Ujvala is not an accredited Certification body under this scheme, Ujvala is trying to adopt an assessment of data transfer mechanism so that it can be incorporated as an assessment criteria.
Ujvala will therefore introduce a “Data Importer Assurance Certification” which a data importer may share with the data exporter as an extension of the DTS-GDPR service. We hope that this “Data Importer Assurance Certification” (DIAC) will be both a GDPR Compliance assurance and the Data Importer’s specific assurance to the data exporter about the compliance of the Cross Border transfer requirements.
At present this will be an extension of DTS-GDPR self assessment followed by the Summary Assessment based on the policy documents submitted by the organization.
Naavi