(Continued from the previous article)
P.S: This series of articles is an attempt to place some issues before the Government of India which promises to bring a new Data Protection Law that is futuristic, comprehensive and Perfect.
Naavi.org had been advising the the Privacy Activists who were opposing the PDPB 2019 that it would be wise to accept the version of the Bill that the Government is ready to accept and later on work for improvements through amendments. We know that CCPA went through such immediate amendment and a similar approach could have been taken in India also with the experience of a simple legislation for an year or two. Unfortunately, the Privacy Activists conspired with the Tech companies and mounted an unreasonably harsh and false propaganda against the Bill which was not feasible for the Government to accept. It must be remembered that Government would have been the worst affected if the law had been passed as it was designed earlier since there would have been many cases that would have been mounted on the Government for personal data breach under various schemes just as the Arogya Setu app was once targeted. The attention of the Government would have been drawn to defending the cases including the charge that the law was ultra-vires the constitution and should be scrapped. The Supreme Court would have looked at the complaint seriously and would have made the life of the Government miserable.
Now, by withdrawing the Bill the Privacy Activists have lost and the Government has cleverly gained an edge. The Government now has some understanding of the agenda of the Privacy activists cum Andolan Jeevies and can plan the next version better.
I am reminded of a cricket scene where the intelligent bowler stops before delivering the ball to know what is the mindset of the batsmen, whether he would come forward, move to the off side, or move to the leg side, try a reverse sweep etc., and plans his next delivery. Similarly, the Government now has some idea of the vulnerable areas of the legislation where it will be attacked by the Privacy Activists Cum Andolan Jeevies and plan the next version accordingly.
The discussion on the Shape of things to come will factor in such possibilities since we need to facilitate a legislation in a balanced approach rather than hoping that we will find a “Perfect Legislation” that will be acceptable to all. Even if the Government presents a diamond, the andolan jeevies in India are in such a mindset that they will call it only “Compressed Carbon” and will not accept its value.
We can refer to the article in Indian Express titled ” Govt withdraws data protection bill to bring revamped, refreshed regualtion” dated August 4, 2022 to respond to some of the objections raised in support of the withdrawal and how they can be addressed in the next version.
The first concern to be addressed is for the Bill to be in line with the Supreme COurt judgement of 2017 particularly since Justice D N Chandrachud would be the CJI in the next term when the new version may be challenged in the Supreme Court.
The second concern is the “Certification of hardware” against malware recommended by the JPC.
Third concern is the Local Data Storage requirements which has been the main objection of the Tech industry.
In a similar article on August 6th the data export restrictions were again cited as the main objection of the tech companies. In this article the possibilities of “Trusted Geographies” being identified was indicated. This is nothing different from the “Adequacy” status of the GDPR unless the Government comes up with some innovative way of establishing a “Data Union”, a concept which we shall explore in greater detail. This was part of our recommendations to the JPC and will be elaborated later.
Another point of discussion is to drop the criteria of sensitivity for cross border data transfer and retain it only for penalties.
We need to discuss each of these points in greater detail and let us start with the first aspect which is how to ensure that the legislation is in tune with the Supreme Court judgement.
One of the comments of the Aadhaar judgement that we should take note of is as follows:
“…it is held that all matters pertaining to an individual do not qualify as being an inherent part of right to privacy. Only those matters over which there would be a reasonable expectation of privacy are protected by Article 21”
This is relevant for the definition of the Right to Privacy that needs to be protected and also for the definition of “Personal Information”. In particular, whether “Meta Data” is data about a “Person” is a point of debate.
The first point to be addressed is
“Whether this law should also be the basic “Right to Privacy Protection Act” or restrict itself to “Protection of Personal Data in Electronic form Act”.
Right to Privacy as is understood is “Right to be let alone”. In the Kharak Singh case, it was discussed in the context of “Home as a castle” where “Physical Privacy” is recognized as a “Right”.
In the context of digitization of personal data, the “right to be left alone” can be disturbed by an SMS message or a WhatsApp message or an e-mail from the Internet space. Just as a person sitting at home may feel his privacy disturbed by the loud speaker in the neighbourhood blaring Aazaan, a person sitting quietly at home may feel his privacy disturbed by the messages on the mobile. Unlike the “Aazaan” issue, the “Message issue” is completely in the electronic domain and hence can be addressed through a “Data Protection Law” without the need to protect privacy in the non-electronic space.
“Non Electronic Space” is not limited to the paper world but also extends to the “Oral speech” as explained in the Aazaan example.
Infringement of Privacy through speech or paper documents is different from the infringement through electronic means.
It would be preferable that the Data Protection Law restricts itself to the Data Space and does not attempt to become a “Privacy Act” by itself. In other words it can be a “Information Privacy Protection Act” only and not a “Privacy Protection Act”.
Also, “Privacy” as a mental state of an individual cannot be captured by a Data Fiduciary except as expressed by the individual himself. Hence the dependency on “Consent” for processing of “Personal Data” is critical and cannot be over ridden by an in-determinable responsibility of the data fiduciary to understand what is in the mind of the data principal and design his data protection measures accordingly. This could be an unreasonable expectation that may be beyond the prescription of law.
This thought makes a significant change to the approach of the law as it means that the concept of “Data Fiduciary” should be pushed back to that of a “Personal Data Manager” which is closer to the concept of “Data Controller” in GDPR. Dropping the “Fiduciary” duty of the Data Controller will weaken the “Protection of Privacy” but it would be more transparent to drop what cannot be legislated just to appear the law to be like an election manifesto of promises that cannot be kept.
Hence the scope of the Act should be limited to “Protection of Personal Information in Electronic Form” and nothing else. It should leave out the personal data in paper form or personal data infringement in oral form both of which should be in the domain of the IPC or a different “Right to Privacy Protection Act”.
Alternatively, the envisaged law could be divided into “Chapters” and one chapter may apply to “Protection of Right to Privacy in Non-Digital Space” and the other on “Protection of Right to Privacy in Digital Space”. Other chapters (if one comprehensive law is to be framed) will include the “Security of personal and non personal data”, “Governance of personal data” and “Governance of Non personal data”.
The chapter on “Governance of Non Personal data” will include the recommendations of the Kris Gopalakrishna committee. Chapter on “Governance of Personal Data” will include the “Personal data collection, processing and disposal requirements as well as the special rights of data principals, the minor’s data etc”. It will also include the cross border restrictions.
Essentially the part of current data protection law with respect to “Security”, “Code of Practice” and “Compliance” can be added in the chapter on “Security of Personal and Non Personal Data”. This chapter will also include information security aspects included in ITA 2000 such as the digital signatures, the CERT IN powers, the ITA 2000 compliance requirements etc. (These have been included in our Data Protection Compliance Standard of India already as a compliance requirement).
The telegraph act to the extent of “Digitized communication” automatically falls under the “information security” area and if parts of the Telecom Governance is to be bundled then it should appear in the “Governance of Non Personal data Chapter”.
The Crypto currency regulations are regulations related to Electronic document and can be covered under the Chapter on “Data Valuation and Monetization” which could be a separate chapter that can be referenced both by the Governance of Personal Data and Governance of Non Personal Data.
Along with these Chapters, a “Chapter on Preliminary” issues would be required where the definitions, scope etc could be added. This is also an opportunity to extend this “Information Privacy Protection Law” to cover the “Neuro Rights” so that India leaps ahead of other countries in recognizing the need for “Neuro Rights Protection” as an extended concept of “Privacy Protection through protection of the individual choice including protection of manipulation of the individual choice”.
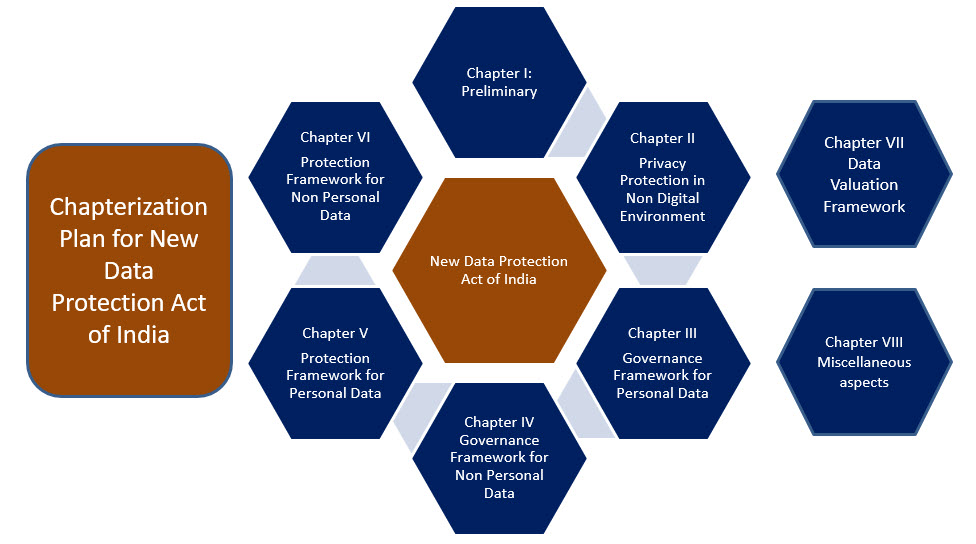
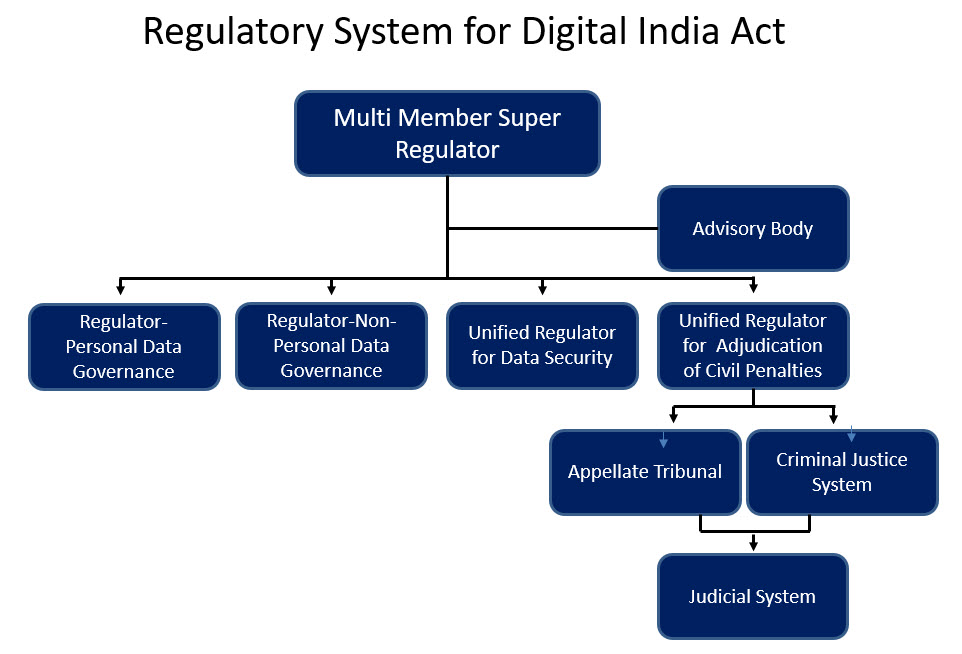
With these discussions, we are arriving at a “Chapterisation” of the New Data Protection Act at the top level leaving sub chapters for further focussed provisions.
The mapping of the chapters therefore looks as under.
Chapter I:
Preliminary (includes basic definitions, applicability related definitions, the Chapter structure, repealing of other laws, segregation of personal data, non personal data, Sovereign Data, Corporate data, community data, Joint data, Transaction data, Neuro data etc, limitations of application to non digital data etc)
Chapter II:
Privacy Protection in Non Digital Data Environment
Chapter III:
Governance Framework for Personal Data
Chapter IV:
Governance framework for Non Personal Data
Chapter V:
Protection Framework for Personal Data
Chapter VI:
Protection Framework for Non Personal Data
Chapter VII:
Data Valuation Framework
Chapter VIII:
Residual Miscellaneous aspects if any
P.S: These discussions are presently for a debate and is a work in progress awaiting more inputs for further refinement. It is understood that the Government may already have a draft and may completely ignore all these recommendations. However, it is considered that these suggestions will assist in the development of “Jurisprudence” in the field of Data Governance in India and hence these discussions will continue until the Government releases its own version for further debate. Other professionals who are interested in participating in this exercise and particularly the Research and Academic organizations are invited to participate. Since this exercise is too complex to institutionalize, it is being presented at this stage as only the thoughts of Naavi. Views expressed here may be considered as personal views of Naavi and not that of FDPPI or any other organization that Naavi may be associated with.
Naavi