(Continued from the previous article)
P.S: This series of articles is an attempt to place some issues before the Government of India which promises to bring a new Data Protection Law that is futuristic, comprehensive and Perfect.
We have been discussing the need for Protection of Privacy Rights to be augmented to protection of Neuro Rights (The series of articles published in this site are also collated at www.neurorights.in).
So far the discussions have been related to the “Brain Computer interface” through electro magnetic radiation that would bring chemical changes in the brain cells leading to specified neuron activity.
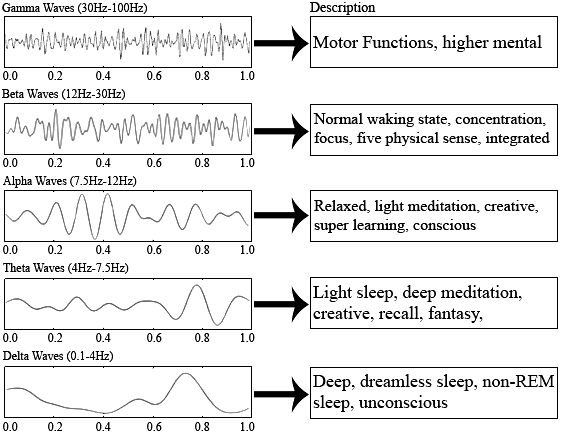
The human brain is said to function with “Brain Waves” which are electro magnetic waves which function in a certain frequency range (or wave length range which is in inverse proportion to frequency) as below.
Externally there are radio waves, Cellular mobile waves and other frequency waves that we come across in the atmosphere. These waves are at a higher wavelength.
5G spectrum which we often hear are in the frequency range of 1GH to 6 GH. (One megahertz (MHz) equals 1,000,000 Hz. One gigahertz is equal to 1,000 megahertz (MHz) or 1,000,000,000 Hz or 109 hertz. In wavelength terms, 1GH is approximately 0.299 metres).
We have heard that radiation from mobiles, mobile towers as well as microwave ovens do affect human brains. Though human body system is tuned to receive certain signals and ignore certain signals the fact that “electro magnetic” is the nature of human brain activity and also the activity of other devices including computers.
The “Brain-Computer interfaces” involving electrodes fixed on top of human skull or chips inside the human skull have gone past animal experimental state and are in advanced state of adoption in our common life. Binaural beats used in music technology is an example on hand.
Current demand for Neuro Rights protection is based on the possibility of manipulation of human brain with implants and other external stimuli which are perceivable by human sensory organs.
Now a new requirement seems to be emerging with scientific developments which indicate the possibility of manipulation of human brain activity without implants and outside the human sensory organs. In other words certain waves which are not heard by our ears or seen by our eyes can be used to manipulate brain activity.
The Privacy concepts such as “Right of Free Choice”, “Expression through a written consent” etc loses meaning when some body can make a human think as per his wish. This is not in the realm of hypnotism or other known forms of psychology through external stimulation. This is a completely new method of intervention of human brain that escapes regulation in any of our known laws.
A serious thought is therefore required to discuss whether our proposed new data protection law should incorporate “Neuro Right Protection” . This will be a point of discussion that may come up during the IDPS 2022.
In our suggestions we added “Neuro Privacy” as a category to be addressed by this new law along with other three forms of privacy namely the Physical privacy (non interference in physical terms), Mental Privacy (Right to be mentally left alone) and Information privacy (Right to manage the use of personal information).
We defined neuro privacy as
(c) “Neuro Privacy” means the choice of an individual to determine to what extent the individual may share his neuro space with others
Perhaps for the purpose of the Act this would suffice. But when it comes to “Reasonable Security to Protect the Neuro Privacy” or “Neuro Privacy by default”, the rules need to address how the neuro intervention devices are regulated.
In one of the recent researches it is contended that “Micro waves” are being sent from drones in an US experimental site and the target population are experiencing mental harassment due to the experiment since they seem to be hearing things. Patents are being claimed for “Microwave Voice to skull technology”.
This patent describes it as an
“invention relates to a hearing system for human beings in which high frequency electromagnetic energy is projected through the air to the head of a human being and the electromagnetic energy is modulated to create signals that can be discerned by the human being regardless of the hearing ability of the person.”
The patent applicant claims
” I have discovered that a pulsed signal on a radio frequency carrier of about 1,000 megahertz (1000 MHz) is effective in creating intelligible signals inside the head of a person if this electromagnetic (EM) energy is projected through the air to the head of the person”
Just as inputs to computer can be given in the form of key strokes or voice commands, in future, Brain-Computer interfaces may operate with sound waves instead of through a remote computing device.
It is this sort of developments that need “Neuro Rights” to be defined now though we may need time on making rules to regulate the protection of Neuro Rights.
Psychiatrists seem to be ignoring the possibility of human brain activity manipulation through sound waves and dismissing the claims of some people in the alleged experimental area as a kind of neurosis.
Watch out for IDPS 2022 where we may take this discussion further… Provided there are speakers who can share their thoughts.
Naavi
Reference
News Report..Video below