The draft of DPDPB 2022 (Digital Personal Data Protection Bill 2022) has been very cleverly drafted by avoiding unnecessary details to give less scope for critics.
The Bill seems to adopt a principle that the Act needs to contain only the broad provisions and many of the details which were part of the earlier bill can be moved to the regulations after the Bill is passed.
Even the public comments to be received upto 17th December will be handled in confidence so that there will not be a disclosure of who suggested what. I would not be surprised if the Bill is passed in the December session of the Parliament itself without waiting upto the February session and the detailed regulations are presented during the February sessions. This is a good strategy to get the Bill moving.
One characteristic of the Bill that strikes the eye is its simplicity. There are only 30 sections instead of the earlier 99 sections. The IT community can feel happy that it is much easier to understand this law than the earlier versions or even the GDPR which had 98/99 sections/articles. The number of definitions have also been restricted to just 17 as against 40 in the previous Bill.
In the process of simplification, some vital aspects have been omitted and they need to be addressed through the subordinate regulations.
Some notable observations are that the definition of harm includes only “bodily harm” and omits “Psychological harm”. Perhaps “Body” should be interpreted as to include the “Mind” and the “Brain” and the definition can be extended to Psychological and Neurological harm as well.
The name as well as the provisions relate to “Digital Personal Data” and hence there may be a reason to feel that the protection of privacy as a fundamental right in oral and paper environment could be considered outside the law. Fortunately, the definition of electronic document used in ITA 2000 is wide and any paper document produced by the use of a computer (including a printer) can be considered as electronic document and brought under this law. Hence all documents processed through computers may be considered as part of this law.
The applicability clause has also been simplified without bringing in the confusion on Anonymised Personal Data.
In the data principal’s rights, the Right to Portability and Right to Forget have been omitted. This could cause some flutter but will be considered good for the industry. Along with the imposition of the duty on the data principal, frivolous complaints which are a bane in GDPR has been eliminated. This could be one of the biggest reliefs to the Data Fiduciaries.
The provision of “Deemed Consent” covers the legitimate interest of a Data Fiduciary and is similar to the previous provisions in PDPB 2019.
Significant Data Fiduciaries need to appoint an Independent Data Auditor but as of now there is no mention of Data Trust Score as a mandatory obligation. But the Auditor may perhaps use such a measurable parameter if he so decides.
The concept of “Privacy By Design” or “Privacy By Design Policy” is conspicuous by its absence though the obligation to be compliant remains.
The Significant Data Fiduciary would also be required to appoint a DPO based in India. Need for him being a Key Management Personnel has been removed but it has been indicated that he is responsible to the Board.
The provisions for transfer of data outside India have been left to be handled by the “Adequacy” decision. Hence the controversy gets buried for the time being.
Similarly the exemptions claimed by the Government has been directly linked to the constitutional exemptions without going too much into the details so that another area of controversy is pushed to the background for the time being.
The Government retains the option to exempt some types of Data Fiduciaries and this can come in handy to provide exemptions to NGOs, Educational Institutions, Charities, Religious institutions etc if need be.
Another provision which was highly controversial earlier and has been skirted now in this draft is the constitution of the Data Protection Authority. The draft has announced that there will be a Data Protection Board which will handle the functions of the erstwhile Data Protection Authority. Again the details on its powers and functions are not included in the Bill. Even the “Code of Practice” mentioned in the erstwhile Section 50 is also absent. Hopefully many of these good things will be introduced through the regulations.
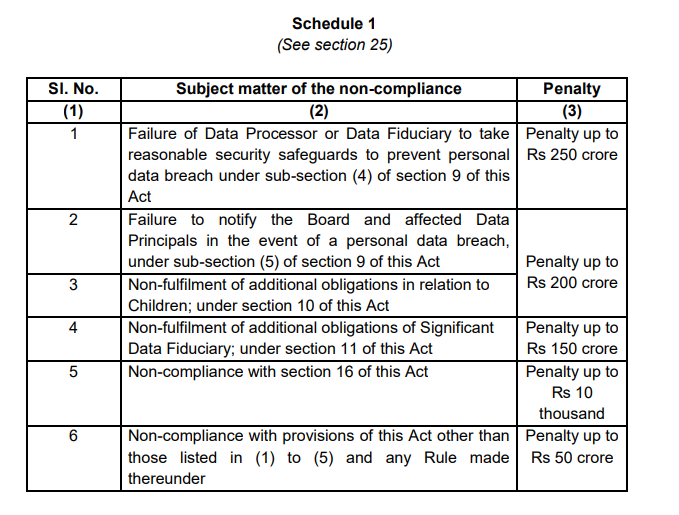
The maximum penalty is fixed at Rs 500 crores and there is no mention of any criminal punishments. The Schedule details 6 sub categories of penalties and penalties are designated as “Upto….” without percentage of turnover. In particular penalty in respect of data breach is upto Rs 200 cores while penalty for non compliance could be higher at Rs 250/- crores. Probably in case of a data breach associated with security non compliance, the penalty could be applied for both. The maximum penalty may however be restricted to Rs 500 crores.
More analysis may follow. However it appears that the Government has ensured that there is very little scope for raising objections at this stage and we need to wait for the notifications to understand the complete implications.
(Comments welcome)
Naavi
Copy of the Act can be perused at www.dpdpa.in