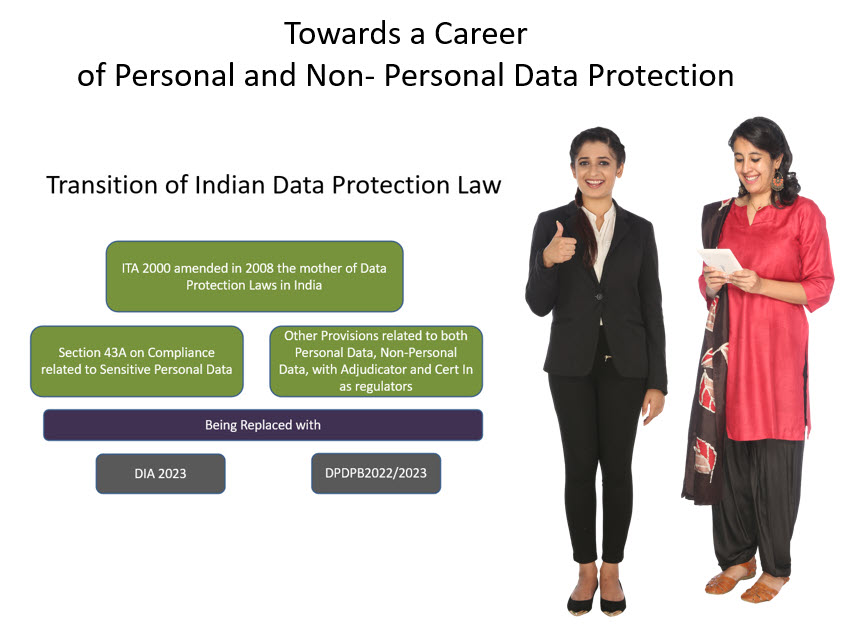
So far in the industry when we speak of “Data Protection” and “Data Audit” we think of Personal Data only. “Non Personal Data Protection” is often considered the domain of IS professionals who are only Tech Professionals. Personal Data Protection Professionals are conscious of laws such as GDPR or DPDPB 2022 while IS professionals are more focussed on ISO standards such as 27001.
The reality however is that in an organization, the Data Pool consists of “Data” which in some context is considered “Personal” and in some context considered as “Non Personal”. According to Naavi’s Theory of data, “Data is in the beholder’s eyes”. It can be personal and non personal at the same time depending on the user. This is similar to the concept of physics which says that light is both a matter and a wave.
A career Data Protection Professional should therefore be conversant with both Personal Data Protection and Non Personal Data Protection. Unfortunately just as the Curriculum in Engineering and Law are mutually exclusive and makes it difficult to produce “Techno Legal Professionals” at the College level, keeping Information Security and Personal Data Protection exclusive makes it difficult to train “Techno Legal Career”.
Now as a pioneering effort, Naavi in association with FDPPI has started a blended course where both aspects of Cyber Laws such as ITA 2000/8 and the upcoming DIA as well as the upcoming DPDPB 2022 and GDPR are being taught to a single group. This is being done by offering a combo Certification program with FDPPI-DNV certification for Data Protection and FDPPI-CLC certification program for Cyber Laws.
No doubt this is a unique and first of the kind experiment of bringing two disciplines into a single platform. We hope this will be appreciated and will become a norm in the future.
Both Programs will be launched on June 17, 2023. The Data Protection program is scheduled as 3 hours sessions on both Saturdays and Sundays for 4 weeks (8 sessions of 3 hours each)
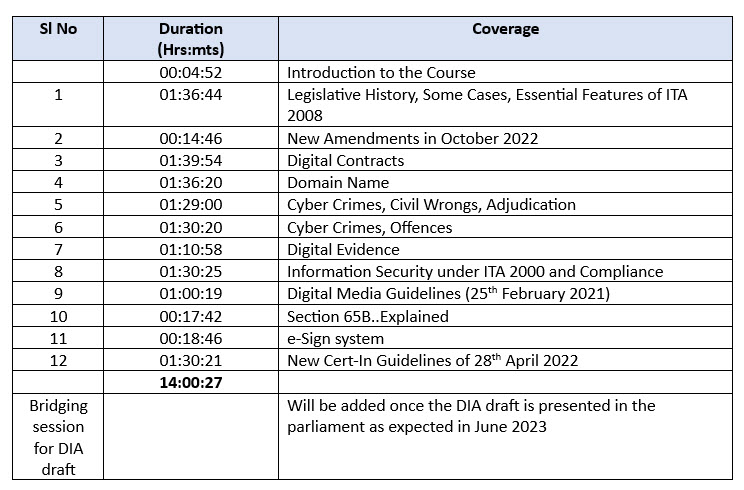
The Cyber Law Course is presented as a hybrid course. It will be formally launched on June 17, 2023 in the afternoon at 3.30 pm. Firstly 14 hours of recorded version of the course would be made available to students. Then during subsequent Saturdays’ 90 minute interactive sessions will be held on June 24 and July 1st and July 8th to discuss the different aspects of the recorded sessions. The June 24th Session would discuss upto Digital Contracts. July 1st session would discuss the Cyber Crimes and July 8th session will discuss the Compliance issues arising from ITA 2000.
It is optional for students to take the combo offer or restrict themselves to one of the courses.
The links for joining the courses are available below: