On 16th of June, 2022, the Government of India issued a Gazette Notification declaring some of the digitals assets of ICICI Bank as “Protected System” under Section 70 of ITA 2000.
At present only a copy of the Gazette Notification regarding ICICI Bank is available in public, though the press reports suggest that HDFC bank and NPCI systems have also been declared as protected systems. There is no information on SBI though SBI maintains most of the Government accounts.
The Meity Website and the egazette.nic.in are yet to publish the notifications for public knowledge.
The ICICI Bank website does not report the development.
This information needs to be notified by ICICI Bank to the stock exchanges and SEBI and so far no such indications are available on the NSE website.
It appears that ICICI Bank is stunned by these developments and does not know how to react.
It is not clear why the Government took this action and whether there was any credible intelligence that the Bank was under attack and NIA has to investigate the same in national security interest. This possibility alone seems to justify why the Government has not notified SBI which is the Bank which holds most of the Government treasury accounts and other assets.
The notification related to ICICI Bank available through another source has been reproduced here.
MINISTRY OF ELECTRONICS AND INFORMATION TECHNOLOGY
NOTIFICATION
New Delhi, the 16th June, 2022
S.O. 2808(E).— In exercise of the powers conferred by sub-section (1) of section 70 of the Information Technology Act, 2000 (21 of 2000), the Central Government hereby declares the computer resources relating to the Core Banking Solution, Real Time Gross Settlement and National Electronic Fund Transfer comprising Structured Financial Messaging Server, being Critical Information Infrastructure of the ICICI Bank, and the computer resources of its associated dependencies to be protected systems for the purpose of the said Act and authorises the following
personnel to access the protected systems, namely: –
(a) any designated employee authorised by the ICICI Bank;
(b) any authorised team members of contractual managed service provider or third-party vendor who have been authorised by the ICICI Bank for need-based access; and
(c) any consultant, regulator, government official, auditor and stakeholder authorised by the ICICI Bank on case to case basis.
2. This notification shall come into force on the date of its publication in the Official Gazette.
[F. No. AA-11018/2/2021-CL&ES]
Dr. RAJENDRA KUMAR, Addl. Secy.
Since this is the first time a private sector network has been declared as a “Critical IT Infrastructure” and Section 70 invoked, it is necessary to study the impact of the declaration on the organization.
We can reproduce Section 70 of ITA 2000 to understand the objective of the section.
Section 7o: Protected system (Amended Vide ITAA-2008)
(1)The appropriate Government may, by notification in the Official Gazette, declare any computer resource which directly or indirectly affects the facility of Critical Information Infrastructure, to be a protected system.
Explanation: For the purposes of this section, “Critical Information Infrastructure” means the computer resource, the incapacitation or destruction of which , shall have debilitating impact on national security, economy, public health or safety.
(Substituted vide ITAA-2008)
(2)The appropriate Government may, by order in writing, authorize the persons who are authorized to access protected systems notified under sub-section (1)
(3) Any person who secures access or attempts to secure access to a protected system in contravention of the provisions of this section shall be punished with imprisonment of either description for a term which may extend to ten years and shall also be liable to fine.
(4) The Central Government shall prescribe the information security practices and procedures for such protected system. (Inserted vide ITAA 2008)
After the amendment of ITA 2000 in 2008/9, Section 70 can be invoked only for “Critical Information Infrastructure”. Critical Information infrastructure needs to be a “computer resource, the incapacitation or destruction of which, shall have debilitating impact on national security, economy, public health or safety.”
A justification of why the declared system is considered “Critical Information Infrastructure” needs to be provided along with the notification. So far we donot see such justification in the notification.
It is necessary for the Government by order in writing to authorize the persons who are authorized to access the declared system and also prescribe the information security practices and procedures for such a protected system.
This written instructions should ideally accompany the notification since any attempt to access the system in contravention of the section could be punished with an imprisonment of 10 years.
In other words the notification is introducing a serious criminal law provision which could impact several persons associated directly or indirectly with the system.
At present the instruction is vaguely expressed in the notification in generic terms such as that the declared systems (resources relating to the Core Banking Solution, Real Time Gross Settlement and National Electronic Fund Transfer comprising Structured Financial Messaging Server,) may be accessed by
(a) any designated employee authorised by the ICICI Bank;
(b) any authorised team members of contractual managed service provider or third-party vendor who have been authorised by the ICICI Bank for need-based access; and
(c) any consultant, regulator, government official, auditor and stakeholder authorised by the ICICI Bank on case to case basis.
In other words the notification is authorizing ICICI Bank to designate the employees or contract persons any consultant, any regulator, any government official, any auditor and any stakeholder authorized by the Bank . The “Stakeholder” may include the customers of the Bank who have to access the CBS system for managing their accounts.
The order therefore abdicates the responsibility of the Government and delegates the powers under the section to the Bank itself.
This appears to be ultra-vires the Act.
On 22nd May 2018, Meity had notified (S.).2235(E) the information Security Practices and Procedures for Protected system.
Now this notification will be binding on ICICI Bank and over ride any other policy that may be in place.
One of the requirements of this policy is that the Bank should constitute an Information Security Steering Committee (ISSC) which should include a representative/s of CERT IN, the Director General of which has been declared as the Nodal officer NCIIPC under Section 70A and 70B of the ITA 2000.
The detailed IS policy as provided in the notification of May 2018 needs to be implemented by the CISO of the Bank who should continuously report to the CERT-IN.
In other words, the CISO of ICICI Bank will now be considered as a subordinate of the CERT-IN and CERT-IN effectively takes over the responsibility for guiding the bank on all its IS measures.
This arrangement is similar to the system where Financial Institutions nominate their representatives in the Boards of companies which they have financed and perhaps turned sick.
In other words, the Government of India has expressed loss of confidence in the ability of the Bank to maintain the security of its systems and found it necessary to exercise a direct supervision.
The “Access Control” mechanism of the Bank will now come directly under the scrutiny of the CERT IN.
The current vague instructions in the Gazette notification which allows any ‘Tom Dick and Harry’ to access the system is highly dangerous to the CERT In since it now becomes answerable to any system intrusions.
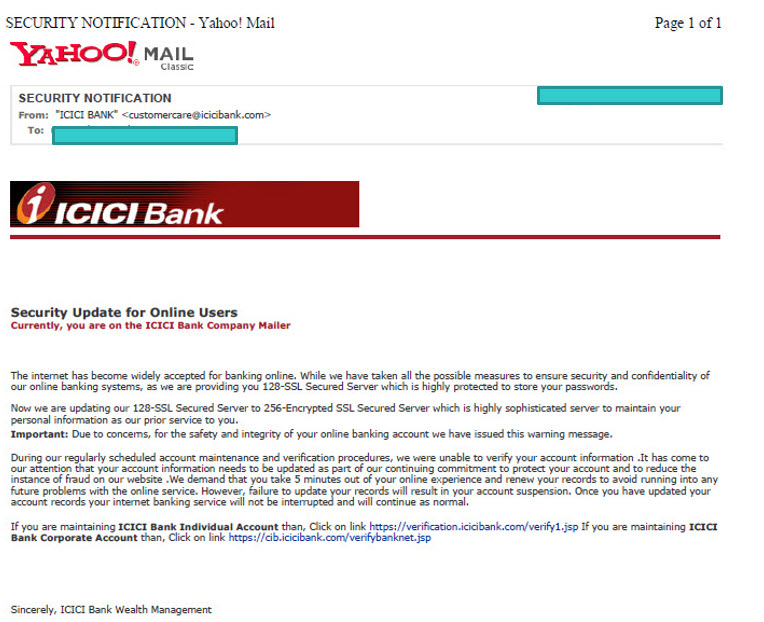
The undersigned has brought a sample of an intrusion to the notice of CERT IN and sought its reaction to the same. This refers to an e-mail which the Bank has identified as a “Phishing Email” which however indicates that the phishing URLs are hosted in the ICICI Bank server itself.
The email is reproduced here for the information of the security professionals
One can observe the URL https://verification.icicibank.com through which the malicious web page appears to have been has been activated.
Now such incidents become the responsibility of CERT IN and if they fail to exercise adequate control on such happenings, the officials of CERT IN would be liable for their negligence.
Further, if Section 70 is invoked on ICICI Bank, HDFC Bank today, there is no reason why it should not be invoked on SBI or PNB or even large hospital chains etc.
Whether CERT IN be able to handle the responsibilities of multiple large private companies is a moot question. Perhaps they need to expand their work force several times to handle such responsibilities.
We shall watch the developments of how this new trend of Government Security infrastructure being extended to protect private digital assets work on the ground.
I wish a proper assessment of the Risks to CERT IN arising out of such responsibilities had been made before such a momentous decision was taken.
(Comments invited)