In continuation of our earlier articles explaining the PDPSI-GDPR that encompasses the ISO 27701 and BS10012, we shall now look at the first of the six fundamental requirements listed earlier for PDPSI namely the implementation responsibility.
A) Define Implementation Responsibility unambiguously with top management involvement
B) Define the scope of implementation in terms of the laws that it needs to address
C) Incorporate measurability in the form of a Data Trust Score or its equivalent
D) Incorporate Privacy by design through out the life cycle of personal information that the organization may encounter
E) Define the implementation charter signed off by the organization at the highest level
F) Incorporate an appropriate certification process –to meet the annual and sub annual requirements of Data Audit as required under the Indian laws
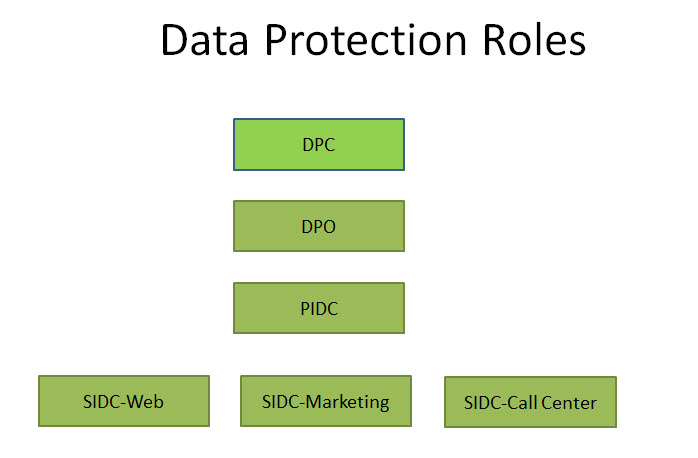
PDPSI suggests as in other frameworks that there would be a Data Protection Committee (DPC) appointed by the Board which will have at least one of the Board Members as part of the committee, preferably the independent Director.
There will be a designated DPO or Data Protection Officer (or a compliance officer if DPO is not mandatory) who will be part of the DPC.
Beyond these two Governance roles, PDPSI differs from all other frameworks in identifying a “Distributed Model of Data Protection”.
What this model suggests as an optional implementation specification is that the organization should identify the “Data Gates” in the organization through which personal data comes in either in one full set or in individual personal data elements.
In the simplest sense there could be a web page on which there is a form for submission of personal data after accepting the “Privacy Policy”. In such a case the entire set of personal data comes in one bunch and there will be one internal executive who receives it first in the company before transferring it to different process owners. That person will be recognized as an “Internal Data Gate Keeper” and will be responsible for receiving it and tagging it appropriately before releasing it to the rest of the processes. He has to identify if which is the applicable law, whether it is the data of an employee or not, whether it is sensitive or not, whether it belongs to a minor etc and add the appropriate tag before committing it to the internal data base, and simultaneously erasing from his cache space.
Where the personal data comes in an unstructured form the receiver will have the responsibility of transferring it immediately to the appropriate person within the organization where the information tagging can be made and at the same time deleting the personal data at his end. To the extent that he has the control of the personal data as a receiver and until he removes it as per the policy of the organization, he would be responsible for data protection and hence he would be an “Internal Data Controller” just like the “Data Gate keeper” who receives the web forms.
The receivers of personal data by virtue of their activities as either the web master or HR executive etc, may be referred to as a Subordinate Internal Data Controller as distinguished from the “Principal Internal Data Controller” who maintains a “Pseudonymzation Gateway” which we shall discuss separately.
 Thus the Governance model recommended under PDPSI incorporates the involvement of the top management along with a distribution of responsibilities. The principle here is that though externally the DPO holds the responsibilities for data protection, internally every employee who has access to personal data will be a subordinate internal data controller. Only those who handle de-identified or anonymized personal data escape the responsibility for personal data protection.
Thus the Governance model recommended under PDPSI incorporates the involvement of the top management along with a distribution of responsibilities. The principle here is that though externally the DPO holds the responsibilities for data protection, internally every employee who has access to personal data will be a subordinate internal data controller. Only those who handle de-identified or anonymized personal data escape the responsibility for personal data protection.
In this model therefore a Work From Home employee is the “Data Protection Manager” for whatever personal data he manages and he has to apply all precautions to secure the data as required.
To the extent possible, it is the responsibility of the technical team to create an architecture where personal data is centralized so that portability and right to forget can be effectively handled as well as implement the Pseudonymization aspects that are discussed in the following article.
The PDPSI-GDPR will also adopt the above Governance structure which is a step above what ISO 27701 or BS 10012 may expect.
Naavi







