Naavi.org has been in the forefront of discussions on Cyber Crimes, Data Security, Compliance requirements etc. The objective of all this is to ensure that “Digital India” does not suffer from the lack of security that is in the DNA of online transactions.
In this journey towards “Secure Digital India”, we need to ensure that the digital payment systems are properly secured. In this process, internationally there have been several initiatives such as the ISO 27001, PCI DSS, SET protocol for card processing, 3-D Secure and its adaptations by VISA, Masters, Amex etc.
In India we have the RuPay scheme which has been conceived to provide a domestic system to enable Indian Banks and financial institutions to participate in the electronic payments market. The Rupay-e-Commerce architecture takes into account the three domains of the issuer, NPCI and the acquirer. The NPCI operates the PaySecure system and the NPCI switch and enables the authentication of the transactions.
The RuPay system has the potential to be a popular global brand like the VISA and Masters. Similarly the authentication system that Rupay adopts also has a potential to be a global system.
India has an advantage that is not available to other countries in the form of the Aadhaar identification system. Though the Supreme Court has placed some curbs on the innovative use of the Aadhaar for authentication by private players, there are acceptable work -arounds and even the possibility of convincing the Supreme Court on specific national security projects for the use of Aadhaar.
If we can use both the Aadhaar network and the NPCI together, it may be possible to enhance the security of online payment systems to a level which could be better than other existing systems.
While the 3-D secure system has the 3 domains namely the acquirer domain, issuer domain and the interoperability domain, which has also been used in the PaySecure architecture of NPCI, it may be possible to look at a four dimensional system (4-D Secure) based on the following constituents.
-
- Consumer
- Merchant
- Banking/Financial institutions
- Technology
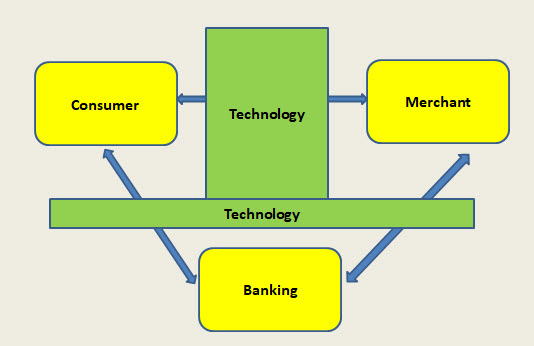
In this model there are four responsibility centers. The Technology is the “Interoperability domain” managed by say NPCI. The Banking is the domain of all card issuers and payment system managers. The Consumer and the Merchant are the basic originator and destination of the underlying transactions.
This model recognizes that “Technology” is the interface between the different legal responsibility centers. In the first leg of the transaction, the transaction originated by the Merchant has to be authenticated by the Customer or vice versa.
In the second leg, the financial part of the transaction originated by the card owner or the Merchant has to be authenticated by the card issuing Bank/his agent .
If the origination of the financial part is a “Pull Transaction”, the Merchant sends his request to the acquiring Bank. If it is a “Push” transaction, the customer sends his request to the card issuing Bank.
The Technology Provider can act as an agent of the Card Issuing bank or the Acquiring bank. The Technology provider can use the UIDAI authentication service in any permitted form. In case of high value transactions, the full e-KYC formality can be invoked. In other cases simple random multi factor parameter check can be used. The identity parameter input if taken in the form of Virtual Aadhaar at the Merchant’s website, it may be within the current directions of the Supreme Court.
Other options including collection of the identity parameter by the Banking system instead of the Merchant or by the UIDAI itself or by NPCI as an agent of UIDAI can be considered and brought into the protocol.
The above is a thought which may be refined by technology experts. However the essence of this suggestion is that we can develop an online payment architecture which is unique to India and if it gets traction, develop similar standard models elsewhere where the UIDAI type of authentication is substituted by some other acceptable trusted third party authentication acceptable to the Banking system or the Card issuer consortium.
I invite technology specialists to improve upon this model if possible and take it forward. I urge NPCI to take the lead in this direction by forming an expert committee along with UIDAI authorities and the MeiTy and examine the possibilities.
Naavi
Reference Articles
Principle of Secure Technology Adoption…creating a secure ecosystem for cyber transactions
Will Rupay challenge VISA/Master and be a global brand?






