In recent days, “Ransomware” has become a global threat to IT and requires some strong counter measures to be undertaken. A few months back, ransomware attack had been reported in Hyderabad and more recently, I came across an incident in Coimbatore where a corporate entity faced a ransomware attack. What is also threatening is that “Ransomware Kits” appear to be afloat for sale in the darkweb and more and more misguided persons may be tempted to buy and use “RansomWare as a Service” (RaaS).
Before this Ransomware virus spreads into an epidemic, we need to act decisively and take it under control. In particular, I request men in the Police force to set up special investigation teams to crack the reported cases and my first such request is for Police in Coimbatore where a report has popped up.
“RansomWare” by definition can be any “Computer Contaminant” (Call it Virus or Trojan if you like) that encrypts the user’s data and demands payment of ransom for unlocking.
The extortionist here is not interested in “Data Theft” and “Ex filtration” of data so that some Data Leak Prevention (DLP) defenses may not be able to identify the malicious activity. But the “Encryption Process” should be otherwise detected by a good Malware detection software if it is not a zero day threat. Since the early days of ransomware, most anti virus companies have tried to address the threat and identified specific “Ransomware Removal Tools”. (Refer this article: 7 Best Ransomware removal tools..). But like in the case of other viruses, the fight is continuous and will go on. Users need to be aware that despite the efforts of having the best antivirus software and managing its timely updations, risks still remain and need to be addressed on a war footing.
Any threat mitigation effort has to start with improving the awareness about the threat and hence we need to know more about the threat by creating an awareness about the threat amongst all the IT users in the organizations including the top management personnel who are as vulnerable as anybody else.
According to a recent note from US Government, in US issued by HHS in the context of HIPAA Compliance, there have been 4000 daily ransomware attacks since early 2016 (300% increase since 2015) indicating the acceleration of the malicious activity. (See the Factsheet here).
The threat of Ransomware in India is grave and our Corporates need to build a robust defense system to mitigate the risks.
I wish all the corporate managers go through this informative article, “Ransomware-Practical view, Mitigation and Prevention tips” by Mr Tal Eliyahu. Microsoft has also released a guideline that is useful to read. ( Read Microsoft Note on Ransomware here).
The essence of the defense is to ensure that the possibilities of infection in the first place is reduced.
The first defense is ofcourse to equip oneself with a good Firewall and Anti malware software that can filter known 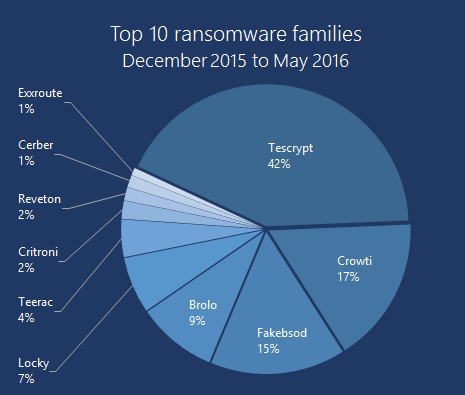 threats. Keeping such software updated and properly configured goes without saying. The accompanying diagram (courtesy-Microsoft) shows the types of ransomware that we may encounter.
threats. Keeping such software updated and properly configured goes without saying. The accompanying diagram (courtesy-Microsoft) shows the types of ransomware that we may encounter.
The infection may also occur due to visiting of unsafe or fake websites through the network, opening of e-mail attachments, clicking on malicious links in social media or even using a USB drive. Obviously, these are threats about which we are aware and have been discussing with our employees for a long time.
But what has changed is that the risks have grown bigger and crippling and this has to be driven home to the users. It is no longer fun to occasionally flout the security norms since virus infection is only a “Probability”.
We need to presume that the “Probability of Infection is always One”.
The second line of defense is therefore to drill home the need to adopt a safe IT usage culture in the organization. I advise every organization to conduct an exclusive training session on the threat of ransomware and obtain a written commitment from every employee that he is aware of the threat and will take steps to ensure that he will secure himself and the organization against the threat.
The third line of defense is for the system administrators to ensure that the “Backup Process” is as good as it can be. Yes this will involve costs but it is better to invest here rather than pay the ransom in future.
How To Respond?
Notwithstanding the measures taken to prevent a ransomware attack, it is an unenviable dilemma that a company faces when it is actually confronted with a situation where it has to take a decision whether to Pay or Not. Obviously, the decision is dependent on the loss that the company has suffered. If it has not backed up its data and has been caught in the attack, then it has to evaluate how to extricate itself out of the situation.
Try all the removal tools that you may be aware of so that you will be able to extricate yourself if you are lucky.
Never hesitate to call in the Police. You need their assistance and they need your cooperation for accumulating knowledge to prevent such happenings in future. Police can be of real help as I have indicated separately later in this article.
Assuming that the removal tools fail or there is no more time to try, the management may be forced to admit defeat and pay.
Once a victim agrees to pay, it means that the attacker feels the kick of success and will continue his exploitation of the same customer in future or others. It is like feeding the hungry devil who would ask for more.
However, it is not always possible to be obstinate and take the moral high ground to say that I will never pay. If the loss is unbearable, then the choice is “Pay and Survive to fight another day”.
There is no guarantee that once a payment is made, the attacker will oblige with a decryption key but it is the risk that some may have to take.
The Penance there after
It is however necessary to remember that the quality of the management is revealed not because they succumbed to the threat and paid up, but by the measures they take soon after. If for whatever reason one agrees to pay, then the victim has to take some urgent steps to correct their past mistakes by measures such as the following.
a) Create a “Clean” backup of data which does not have the infection. Ensure that the decrypted data is analyzed to remove any lurking trojan which may get activated once again.
b) Try to identify the source of infection and root it out
c) Harden the security measures so that the possibilities of re-infection is eliminated.
What the Police Can do
We should remember that ransomware attack succeeds only when the attacker successfully gets the payment for his efforts. This means that there has to be a reverse flow of money from your account to the other and here in lies the small possibility of detection and bringing the culprit to book.
According to Indian Law, “Ransomware Attack” can be classified as “Cyber Terrorism” since it strikes terror in the minds of a section of people, causes damage to property and uses denial of access and unauthorized access as an attack strategy. According to Section 66F, the perpetrator of a ransomware attack can be imprisoned for life under section 66F.
I wish that Police first takeout an advertisement to publish this so that the India based extortionists at least will realize that buying a ransomware kit and sending it across to a few to try their luck is as dangerous as playing with a terror game or a drugs game and land them in Jail without Bail.
Though this may not deter the foreign attackers who work with Bitcoin payments, at least we will reduce the number of such attacks in India.
When such an attack materializes, the attacker will leave some trace through his e-mail (as in the case of the Coimbatore attack) or destination payment agent. There will be many “Intermediaries” who would be used by him to encash on his crime. Police need to neutralize them ruthlessly first by seeking their assistance and if they refuse to cooperate, applying section 69,69A and 69B provisions of ITA 2008 and locking up if necessary the executives of these firms for 7 years as the law provides. ( I suppose this will not be necessary if sufficient awareness of this threat is built up again through advertisements by the Police).
Since the tracing of the criminal can happen only during the payment cycle, I request all victims to contact the Police even if they are not confident that they will be of help in decryption. Police also should realize that even if they are not capable of decryption, they may be efficient enough to track the flow of money and eventually catch the criminal.
I wish that Police in each state as well as CBI set up a special “Ransomware Cell” to address this menace. Magistrates should be made to realize that “Ransomware is Cyber Terrorism” and they have to be strict in punishing the criminals once they are caught.
I sincerly believe that it is through such deterrance only that we may be able to slow down the spread of ransomware and we need to work towards this goal.
I call upon Coimbatore Police where one of the crimes have now been reported set up the first “Ransomware Task Force” in India and take up the reported case.
Simultaneously Bangalore Police which has the necessary expertise at the Cyber Crime Cell to also consider setting up a task force to build expertise in solving ransomware attacks if and when it is reported to them.
I look forward to their response.
Naavi
Message for the Public
RansomeWare attack is Cyber Terrorism in India..There can be Life Imprisonment and No Bail for the suspects. Intermediaries who donot cooperate in investigation and donot put in practice “Due Diligence” and “Reasonable Security Practice” to prevent ransomware attacks are liable for 7 years imprisonment for their Directors and Executives.
Related Information
Stellar Data Recovery : Speaks of No Recovery-No Charge Policy
TrendMicro Screen Unlocker Tool
Ransomwarre Resistance from Kasparesky
Bitdefender FBI Ransomware infection
List of Free Ransomware Decryptor Tools from windowsclub.com
List of Tools from majorgeeks.com







